Contents
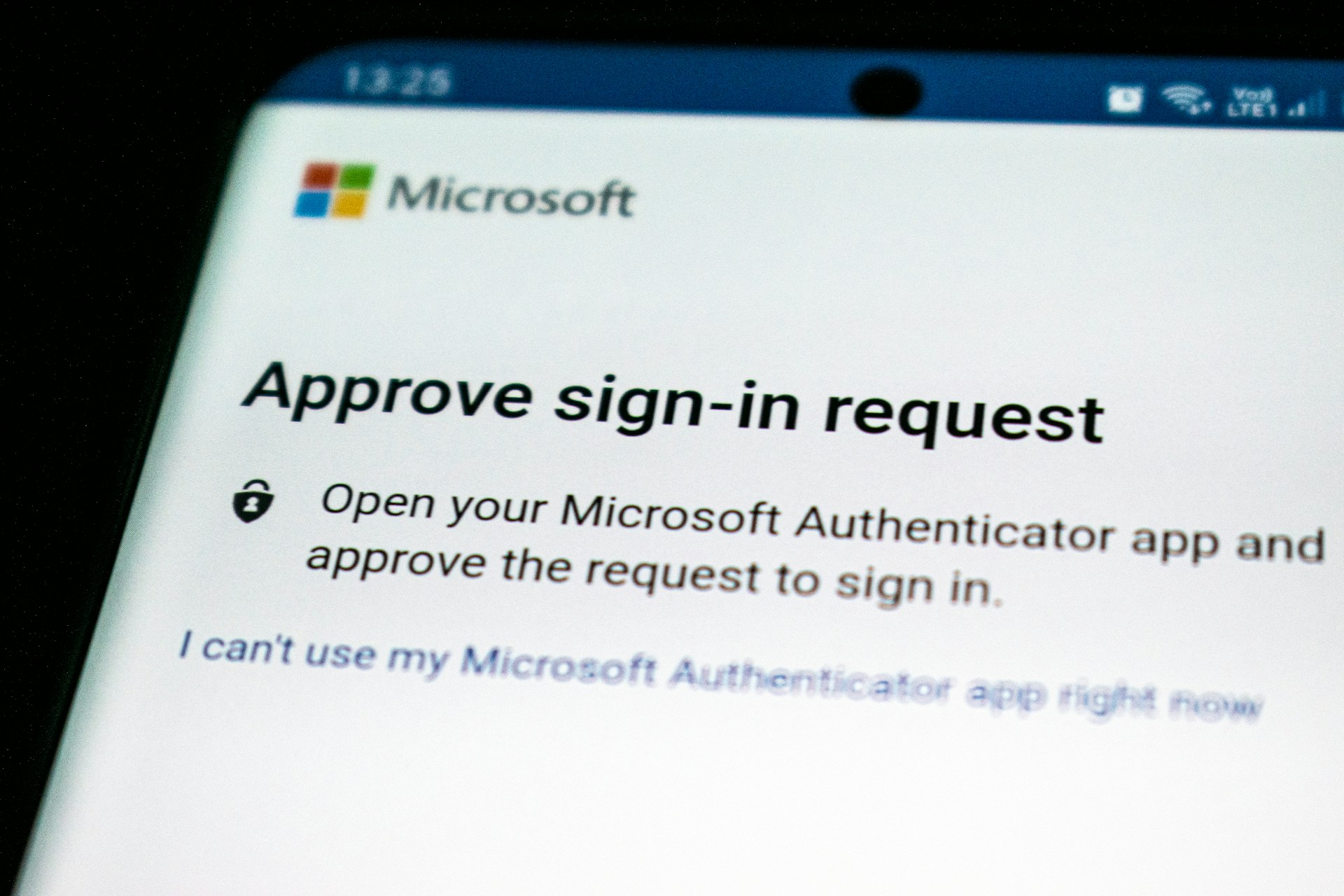
Most account hacks start with a single stolen password. If that thought makes you uneasy, there’s a straightforward way to cut risk dramatically: add a second proof of identity. Two-factor authentication (2FA) layers a second check on top of your password so a stolen credential alone won’t open the door.
Passwords are portable, reusable, and often weak. Adding 2FA changes the attacker’s calculus: they need something you have in addition to something you know. That’s a far higher bar.
2FA reduces account takeover risk and blocks many automated attacks. For example, security teams report authentication methods beyond passwords stop the vast majority of mass credential-stuffing attempts.
Microsoft found that using authentication methods beyond passwords blocks over 99.9% of account attacks that use leaked credentials.
Beyond raw protection, 2FA is a baseline requirement for many services, compliance frameworks, and business accounts. Treating it as optional leaves you exposed.
Not all 2FA methods are equal. Pick the one that fits your threat model and device ecosystem.
SMS codes: You receive a numeric code by text message. Easy, but vulnerable to SIM swap and interception.
Time-based one-time passwords (TOTP): Short codes generated by apps like Google Authenticator, Authy, or Microsoft Authenticator. More secure than SMS when backed up properly.
Push-based authentication: A service sends a push prompt to your device to approve or deny sign-ins. Convenient and phishing-resistant if implemented well.
Hardware security keys: Physical devices such as FIDO2 or U2F keys (for example YubiKey) that provide strong, phishing-resistant authentication.
Biometrics: Fingerprint or face unlock used as a second factor on supported platforms. Convenient but tied to device hardware and OS security.
Ask three quick questions: What devices do you use most? How sensitive are the accounts? How comfortable are you with extra setup and recovery planning?
For everyday consumer accounts on phones and laptops, TOTP apps or push prompts balance security and convenience.
For high-value accounts (email, cloud storage, financial), hardware security keys offer the strongest protection against phishing.
If you need remote backup across devices, choose an authenticator that supports encrypted backups.
For authoritative guidance about authentication best practices consult the NIST authentication guidelines, which explain modern, risk-based approaches to multi-factor verification.
Smartphones are the hub for most people’s 2FA. Here are repeatable steps that apply to most services.
Open the account settings or security section of the service you want to protect.
Find the option named Two-step verification, Two-factor authentication, or Security.
Choose your preferred method: SMS, Authentication app, or Security key.
Follow prompts to scan a QR code or register a device. Keep recovery codes in a secure place.
Here are links to platform-specific instructions: Google's 2-Step Verification setup and Apple's two-factor authentication overview. Both services provide step-by-step flows built for mobile devices.
Authentication apps generate short-lived numeric codes that replace SMS. They’re widely supported and more secure when properly backed up.
Install a trusted app: Authy, Google Authenticator, or Microsoft Authenticator.
When a site shows a QR code, scan it with the authenticator app to add the account.
Record and store the recovery or backup codes the site provides at setup.
Authy supports encrypted multi-device backups; Google Authenticator historically lacked cloud backup but now offers device transfer tools. Choose an app that fits your tolerance for device loss recovery.
oathtool --totp -b JBSWY3DPEHPK3PXP
The example above shows how a TOTP code can be generated from a base32 key using oathtool for advanced users managing local keys.
Hardware keys implement public-key cryptography and are the most resistant to phishing. They are recommended for administrators, developers, and anyone with high-value accounts.
Choose a modern FIDO2-compliant key from reputable vendors. Register the key in the account's security settings by inserting or tapping it when prompted.
Buy a key that supports USB-A, USB-C, and/or NFC for mobile compatibility.
Register the key in the service’s security or 2FA section, giving it a recognizable name.
Keep a secondary key in a secure location as a backup in case the primary key is lost.
For vendor specifics, see Yubico's hardware key details and the WebAuthn specification for technical background.
Desktop setups often mirror mobile flows, but take advantage of browser security features and extensions.
Use a password manager with built-in TOTP support so codes sync between devices securely.
When prompted to confirm new devices, prefer push prompts or security keys over SMS.
Register recovery options immediately: a secondary email, backup codes, and an extra security key.
Tip: Modern browsers support security keys and the navigator.credentials.create API for seamless hardware key registration.
Most lockouts result from lost phones or discarded recovery codes. Plan recovery carefully so you don’t lose access when you need it most.
Save printed or encrypted recovery codes in a secure physical location or in an encrypted password manager.
Store a secondary verification method such as a backup phone number or alternate authenticator app.
Keep a secondary hardware key in a safe place, separate from the primary key.
Recovery planning is not glamorous, but it prevents the much larger problem of permanent account lockout.
To get the most from 2FA, combine techniques that reduce phishing and human error.
Use phishing-resistant methods such as security keys or push-based approvals when possible.
Enable 2FA on every account that stores sensitive data, including email, cloud drives, banking, and social media.
Keep recovery codes offline and update them if you suspect compromise.
Combine with a password manager to use unique, strong passwords for each account.
Remove old devices from account access lists when you upgrade phones or sell hardware.
For enterprise environments or developers, the OWASP two-factor authentication cheat sheet explains implementation and threat considerations in detail.
Problems arise, but many are easy to fix if you know the common causes.
Incorrect time-based codes: Ensure your device clock is set to automatic time synchronization.
Lost authenticator app: Use stored recovery codes or alternate registered methods to regain access.
SIM swap suspicion: Contact your carrier immediately and move to app-based or hardware-key 2FA to avoid SMS dependence.
Hardware key not recognized: Update OS and browser, and check for driver or firmware updates from the vendor.
Proactive maintenance like periodically auditing your 2FA methods and removing unused devices reduces long-term risk.
Seeing how 2FA helps in practice clarifies the trade-offs between convenience and security.
Small business owner: A stolen password used against a cloud accounting service could be catastrophic. Adding hardware keys for admin accounts restricts lateral movement if an employee’s credentials are exposed.
Frequent traveler: Using an authenticator app with encrypted cloud backup prevents lockouts when changing SIM cards abroad.
Developer or admin: Register two hardware keys and keep one offline. This preserves access when the travel key is lost or stolen.
These approaches map to different threat models and budgets but share common principles: reduce reliance on SMS, prepare for device loss, and register backups.
Power users can adopt stricter policies and tools to minimize attack surfaces.
Enroll accounts in enterprise single sign-on (SSO) systems that use certificate-based or FIDO2 authentication.
Require conditional access policies: restrict logins by location, device compliance, or risk score.
Use hardware-backed keys with multi-protocol support to authenticate across services without repeating setup.
For developers building authentication flows, refer to the WebAuthn spec for standards-based implementations that support strong, phishing-resistant authentication.
Passwords alone are no longer sufficient. Adding a second factor—ideally a TOTP app, push prompt, or hardware key—reduces the chance of account takeover and increases peace of mind.
Start with your most sensitive accounts: email, financial, cloud storage, and admin consoles.
Prefer phishing-resistant methods like hardware keys or push approval when available.
Plan recovery carefully so you don’t trade a security improvement for a lockout risk.
Now that the path is clear, enable 2FA on your high-risk accounts this week, register backups, and adopt a password manager to keep credentials unique and manageable. These steps will materially reduce your exposure and make account compromise far less likely.